Florida’s Anti-Encryption Bill Is a Wrecking Ball to Privacy. There's Still Time to Stop It.
Apr. 22nd, 2025 10:34 pmWe've seen plenty of bad tech bills in recent years, often cloaked in vague language about "online safety." But Florida’s SB 868 doesn’t even pretend to be subtle: the state wants a backdoor into encrypted platforms if minors use them, and for law enforcement to have easy access to your messages.
This bill should set off serious alarm bells for anyone who cares about digital rights, secure communication, or simply the ability to message someone privately without the government listening. Florida lawmakers aren’t just chipping away at digital privacy—they're aiming a wrecking ball straight at it.
SB 868 is a blatant attack on encrypted communication. Since we last wrote about the bill, the situation has gotten worse. The bill and its House companion have both sailed through their committees and are headed to a full vote. That means, if passed, SB 868 would:
- Force social media platforms to decrypt teens’ private messages, breaking end-to-end encryption
- Ban “disappearing” messages, a common privacy feature that helps users—especially teens—control their digital footprint
- Allow unrestricted parental access to private messages, overriding Florida’s own two-party consent laws for surveillance
- Likely pressure platforms to remove encryption for all minors, which also puts everyone they talk to at risk
In short: if your kid loses their right to encrypted communication, so does everyone they talk to.
There Is No Safe Backdoor
If this all sounds impossible to do safely, that’s because it is. There’s no way to create a “just for law enforcement” access point into encrypted messages. Every backdoor is a vulnerability. It's only a matter of time before someone else—whether a hacker, abuser, or foreign government—finds it. Massive breaches like Salt Typhoon have already proven that surveillance tools don’t stay in the right hands for long. Encryption either protects everyone—or it protects no one. We must protect it.
Encryption Matters—Especially for Teens
Encryption isn’t optional in today’s internet—it’s essential. It protects your banking info, your health data, your personal chats, and yes, your kids' safety online.
SB 868 pretends to “protect children,” but does the opposite. Teens often need encrypted messaging to talk to trusted adults, friends, and family—sometimes in high-stakes situations like abuse, mental health crises, or discrimination. Stripping away those safeguards makes them more vulnerable, not less.
Investigators already have powerful tools to pursue serious crimes, including the ability to access device-level data and rely on user reports. In fact, studies show user reporting is more effective at catching online abuse than mass surveillance. So why push a bill that makes everyone less safe, weakens encryption, and invites lawsuits? That’s a question we all deserve an answer to.
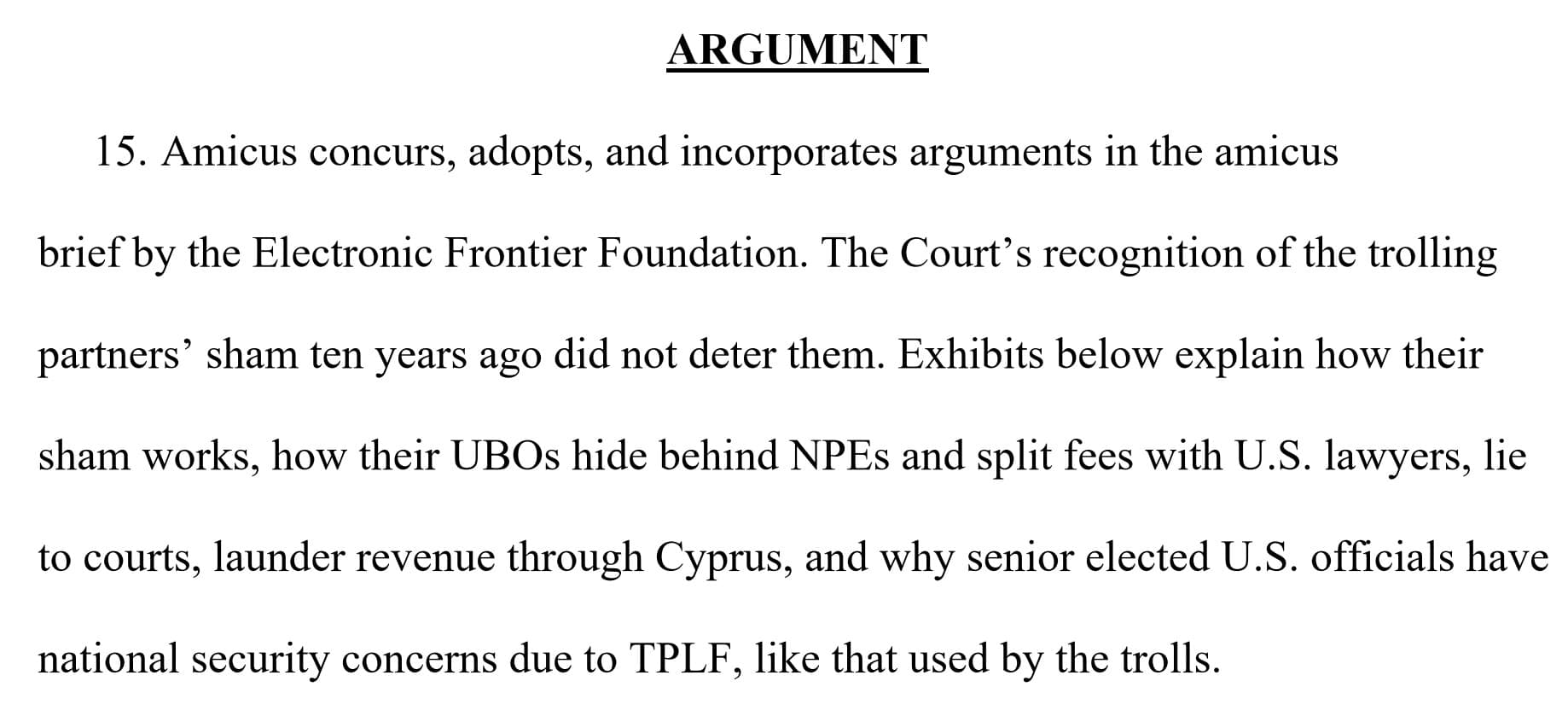
It’s Time to Speak Up
Florida’s SB 868 isn’t just a bad bill—it’s a dangerous blueprint for mass surveillance. Tell Florida Legislators: SB 868 is unsafe, unworkable, and unacceptable.
If you live in Florida, contact your lawmakers and demand they reject this attack on encryption.
If you're outside the state, you can still speak out—public pressure matters, and the more people who call out how egregious this bill is, the harder it becomes for lawmakers to quietly push it forward. Make sure you follow us on social media to track the bills’ progress and help amplify the message.
Privacy is worth fighting for. Let’s stop SB 868 before it becomes law.
What to know about reports RFK Jr. is launching registry to track Americans with autism
Apr. 22nd, 2025 11:21 pmGmail Will Help You Manage All Your Email Newsletters & Spam
Apr. 22nd, 2025 10:11 pmI have a huge problem with my Gmail account. It's filled to the brim with email subscriptions, some of which I subscribed to several years back—and going one-by-one unsubscribing to each is an extremely time-consuming task. Now, Gmail might actually help me fix that problem.
Trump really showed kids 'assassination trading card' at White House Easter event
Apr. 22nd, 2025 10:33 pmSix Years of Dangerous Misconceptions Targeting Ola Bini and Digital Rights in Ecuador
Apr. 18th, 2025 05:55 pmOla Bini was first detained in Quito’s airport six years ago, called a “Russian hacker,” and accused of “alleged participation in the crime of assault on the integrity of computer systems.” It wouldn't take long for Ecuadorean authorities to find out that he was Swedish and an internationally respected free software developer and computer expert.
Lacking evidence, authorities rapidly changed the criminal offense underpinning the accusation against Bini and struggled to build a case based on a mere image that shows no wrongdoing. Yet, Bini remained arbitrarily detained for 70 days in 2019 and outrageously remains under criminal prosecution.
This week, the Observation Mission monitoring Ola Bini’s case is again calling out the prosecution’s inaccuracies and abuses that weaponize misunderstandings about computer security, undermining both Bini’s rights and digital security more broadly. The Observation Mission is comprised of digital and human rights organizations, including EFF. Specifically, we highlight how Ecuadorean law enforcement authorities have tried to associate the use of Tor, a crucial privacy protection tool, with inherently suspicious activity.
Following a RightsCon 2025 session about the flaws and risks of such an interpretation, we are releasing this week a technical statement (see below) pointing out why Ecuadorean courts must reaffirm Bini’s innocence and repudiate misconceptions about technology and technical knowledge that only disguise the prosecutor’s lack of evidence supporting the accusations against Bini.
Let’s not forget that Bini was unanimously acquitted in early 2023. Nonetheless, the Prosecutor’s Office appealed and the majority of the appeals court considered him guilty of attempted unauthorized access of a telecommunications system. The reasoning leading to this conclusion has many problems, including mixing the concepts of private and public IP addresses and disregarding key elements of the acquittal sentence.
The ruling also refers to the use of Tor. Among other issues, the prosecution argued that Tor is not a tool known by any person except for technical experts since its purpose is to hide your identity on the internet while leaving no trace you're using it. As we stressed at RightsCon, this argument turns the use of a privacy-protective, security-enhancing technology into an indication of suspicious criminal activity, which is a dangerous extrapolation of the “nothing-to-hide argument.”
The prosecutor’s logic, which the majority appeal ruling endorses, is if you’re keeping your online activities private it’s because you’re most likely doing something wrong, instead of we all have privacy rights, so we are entitled to use technologies that ensure privacy and security by default.
Backing such an understanding in a court ruling sets an extremely worrying precedent for privacy and security online. The use of Tor must not be up for grabs when a prosecutor lacks actual evidence to sustain a criminal case.
Bini’s defense has appealed the unfounded conviction. We remain vigilant, hoping that the Ecuadorean judicial system will correct the course as per basic tenets of the right to a fair trial, recognizing the weakness of the case rather than surrendering to pressure and prejudice. It's past time for justice to prevail in this case. Six years of a lingering flimsy prosecution coupled with the undue restriction of Bini’s fundamental rights is already far too long.
Read the English translation of the statement below (see here the original one in Spanish):
TECHNICAL STATEMENT
Ola Bini’s innocence must be reaffirmed
In the context of RightsCon Taipei 2025, the Observation Mission of the Ola Bini case and the Tor Project organized a virtual session to analyze the legal proceedings against the digital security expert in Ecuador and to discuss to what extent and with what implications the use of the Tor digital tool is criminalized1. In that session, which included organizations and speakers from civil society from different countries, we reached the following conclusions and technical consensuses:
- The criminal case against Bini was initiated by political motivations and actors and has been marked by dozens of irregularities and illegalities that undermine its legal legitimacy and technical viability. Rather than a criminal case, this is a persecution.
- The way the elements of conviction of the case were established sets a dangerous precedent for the protection of digital rights and expert knowledge in the digital realm in Ecuador and the region.
- The construction of the case and the elements presented as evidence by the Ecuadorian Attorney General’s Office (EAG) are riddled with serious procedural distortions and/or significant technical errors2.
- Furthermore, to substantiate the crime supposedly under investigation, the EAG has not even required a digital forensic examination that demonstrate whether any kind of system (be it computer, telematic, or telecommunications) was accessed without authorization.
- The reasoning used by the Appeals Court to justify its guilty verdict lacks sufficient elements to prove that Ola Bini committed the alleged crime. This not only violates the rights of the digital expert but also creates precedents of arbitrariness that are dangerous for the rule of law3.
- More specifically, because of the conviction, part of the Ecuadorian judiciary is creating a concerning precedent for the exercise of the rights to online security and privacy, by holding that the mere use of the Tor tool is sufficient indication of the commission of a criminal act.
- Furthermore, contrary to the global trend that should prevail, this ruling could even inspire courts to criminalize the use of other digital tools used for the defense of human rights online, such as VPNs, which are particularly useful for key actors—like journalists, human rights defenders, academics, and others—in authoritarian political contexts.
- Around the world, millions of people, including state security agencies, use Tor to carry out their activities. In this context, although the use of Tor is not the central focus of analysis in the present case, the current conviction—part of a politically motivated process lacking technical grounding—constitutes a judicial interpretation that could negatively impact the exercise of the aforementioned rights.
For these reasons, and six years after the beginning of Ola Bini’s criminal case, the undersigned civil society organizations call on the relevant Ecuadorian judicial authorities to reaffirm Bini’s presumption of innocence at the appropriate procedural stage, as was the first instance ruling demonstrated.
The Observation Mission will continue monitoring the development of the case until its conclusion, to ensure compliance with due process guarantees and to raise awareness of the case’s implications for the protection of digital rights.
1. RightsCon is the leading global summit on human rights in the digital age, organized by Access Now. ↩
2. See https://www.accessnow.org/wp-content/uploads/2022/05/Informe-final-Caso-Ola-Bini.pdf ↩
3. The Tribunal is composed of Maritza Romero, Fabián Fabara and Narcisa Pacheco. The majority decision is from Fabara and Pacheco. ↩
Samsung's Glasses-Free 3D Gaming Monitors Are Now Available
Apr. 22nd, 2025 09:32 pmSamsung has released its 2025 Odyssey lineup of gaming monitors. The collection comes with the Odyssey 3D, Odyssey OLED G8, and the wide-screen Odyssey G9. They're pretty pricey, but Samsung is offering $300 Samsung credit for purchasing any new Odyssey monitor until April 27.
What Is Starlink and How Do the Satellites Work?
Apr. 22nd, 2025 09:00 pmBuilding out fiber optic network over thousands of miles to provide internet to millions of people is a difficult, time-consuming, and expensive task. What if you could cut out the physical connections entirely and only use wireless? That is exactly what Starlink aims to do.
Max Will Now Charge for "Extra Members" Like Netflix
Apr. 22nd, 2025 08:56 pmSharing your Max account with someone outside of your household? You're not alone, and Max has a new way to handle it that looks awfully familiar. Just like Netflix, Max is now letting you add an "Extra Member" to your account, but it'll cost you.
Retro Handheld Company Suspends U.S. Shipping Over Controversial Tariffs
Apr. 22nd, 2025 08:45 pmPresident Donald Trump's tariffs continue to cause mayhem upon the gaming industry, disrupting the global economy in the process. As a result, various gaming companies have cranked up their prices, pushed back pre-orders, and even increased how much subscription services would cost players—we're looking at you, Nintendo, and Sony. But they're not the only companies that have responded to Trump's tariffs.
Google Fi Has a New $35/mo 5G Plan and Data-only eSIMs
Apr. 22nd, 2025 08:36 pmThe mobile carrier Google Fi is now 10 years old, and Google is celebrating with a new unlimited plan for $35 per month, eSIMs for data-only devices, and helpful updates to its other plans.
For $20, Anker’s Waterproof Bluetooth Speaker Is an Easy Buy
Apr. 22nd, 2025 08:04 pmWhether you're shopping for Mother's Day or looking for a new portable Bluetooth speaker for warmer weather, my favorite mini speaker is at its lowest price yet. I'm talking about the Soundcore Select 4 Go, which is 41% off for a limited time.
MPA and RIAA Want to be Heard in Crucial DMCA Subpoena Appeal
Apr. 22nd, 2025 08:21 pm Tackling online piracy is a complicated endeavor that often begins with efforts to identify the operators of infringing sites and services. This is also where the first hurdles show up.
Tackling online piracy is a complicated endeavor that often begins with efforts to identify the operators of infringing sites and services. This is also where the first hurdles show up.
Many pirates keep their identities concealed. This applies to the operators of sites and services as well as their users.
This relative anonymity is a nuisance to anti-piracy groups, including the RIAA and MPA. While most online services refuse to voluntarily hand over user details, legal tools can help rightsholders move forward.
In recent years, DMCA subpoenas have established themselves as a key anti-piracy enforcement tool. These requests don’t require any oversight from a judge and are typically signed off by a court clerk. This makes them ideal to swiftly identify online pirates.
DMCA Subpoenas at Risk
Both the RIAA and MPA have used these subpoenas to identify owners of pirate sites and individual infringers. The groups would like DMCA subpoenas, as detailed in DMCA §512(h), to remain in their toolbox but there are concerns that a recent court order could hinder their effectiveness.
The case in point doesn’t involve the RIAA or MPA. It’s a dispute between several independent film companies and Internet provider Cox. The latter successfully objected to a DMCA subpoena which sought to obtain the personal details of numerous alleged BitTorrent pirates.
The main contention in this case is whether DMCA subpoenas apply to residential Internet providers. Cox argued against, describing itself as a mere conduit provider benefiting from the DMCA’s §512(a) safe harbor, which does not require ISPs to take anything down, because the ISP doesn’t store content.
For background, a brief summary of the four types of ISPs under 17 U.S.C. § 512.
– §512(a): transitory digital network communications; services that merely pass on bits and bytes
– §512(b): system caching; services that temporarily store (cache) data
– §512(c): storage of information on systems; services that host data
– §512(d): information location tools; services that connect users to online locations (e.g. social media, search engines)
Last year, the court agreed with Cox’s reasoning and quashed the subpoena. The order concluded that DMCA subpoenas typically don’t apply to DMCA §512(a) services, but do apply to other providers that store or link to infringing content directly.
The film companies, including Capstone Studios and Millennium Funding, didn’t give up. After the motion for reconsideration failed, they filed an appeal at the Ninth Circuit Court of Appeals. Among other things, the appeal argued that Cox also falls under DMCA §512(d), as it can remove or disable ‘references or links’ to infringing content.
In addition, the rightsholders also argue that DMCA subpoenas apply to § 512(a) service providers. Therefore, they say, a DMCA subpoena should be valid for Cox.
MPA and RIAA Want to be Heard
The language of the DMCA can be complex at times and open to interpretation. The film companies hope that they can force a breakthrough via the court of appeals, but an adverse ruling that further restricts the scope of DMCA subpoenas is possible too.
The risk of an adverse ruling clearly has the MPA and RIAA worried. They often use these subpoenas to request information from third-party services such as Cloudflare, social media companies, and domain registrars.
The trade groups previously shared their thoughts in an amicus brief. They didn’t take sides in the dispute, but pointed out that the lower court’s ruling was too broad. Specifically, they questioned the part suggesting that IP addresses may never function as links, within the context of the section 512(d) safe harbor.
MPA and RIAA instead argued that section 512(d) services, which could cover reverse proxy providers such as Cloudflare, can link to pirate websites through IP-addresses.
If the district court’s order stands, the validity of MPA and RIAA DMCA subpoenas may be in question. For this reason, the group urged the court to limit its findings to the evidence at hand, without the contested and presumably unneeded IP-address interpretation.
To further reiterate this position, MPA and RIAA asked for speaking time at a hearing scheduled for June. They request 10 minutes of the court’s time, while keeping the available time for the other parties at 15 minutes each.
“MPA and RIAA invest substantial resources to combat online piracy, including through the use of section 512(h) subpoenas. Because infringers hide under aliases and behind proxies, section 512(h) subpoenas are a key tool to combat online infringement and protect the legitimate creative industries,” the groups inform the court.
“Amici intend to use their time to advocate for reversal or a narrow ruling, preventing unintended consequences for subpoenas and issues not before this Court that could have unintended consequences on the carefully-crafted compromise reflected in the DMCA.”

The court has yet to rule on this request. While the movie companies don’t object, Cox doesn’t want to extend the hearing by ten minutes, but wants the MPA and RIAA to use the film companies’ time instead.
‘Trolls’
Where the MPA and RIAA call for a more narrow and restricted ruling, an additional third-party has submitted an amicus brief that extends far beyond the legal intricacies of the DMCA’s section 512.
That submission comes from Charles Muszynski, who has been embroiled with movie companies and their attorneys for several years. Their dispute started when the movie companies targeted LiquidVPN, which had been purchased by one of Muszynski’s companies.
That particular legal battle is over, but follow-up litigation in international courts continues to this day. According to Muszynski, the movie companies are of a “copyright troll” group that operates a “criminal racketeering and money laundering sham” that he likens to the criminal Prenda Law operation.
These allegations are not immediately relevant for the DMCA subpoena argument. But, for the matter at hand, Muszynski’s amicus brief concurs and adopts the arguments that were previously made by the Electronic Frontier Foundation (EFF) in this case.
EFF also used the “troll” terminology, albeit in a different context and without directly referring to the movie companies. EFF urged the court not to allow copyright holders to issue §512(h) subpoenas to ISPs who simply transmit data, as this could trigger more coercive settlement requests against internet subscribers.
The amicus curiae briefs from both EFF and Muszynski are still listed as pending, so it’s still unknown whether they will be considered by the Court of Appeals. That said, with many eyes on this case, it’s clear that there’s a lot at stake in the upcoming hearing, and in the ruling that will eventually follow.
—
A copy of the MPA and RIAA’s request to participate in the oral hearing is available here (pdf). Muszynski’s amicus curiae brief is available here (pdf)
From: TF, for the latest news on copyright battles, piracy and more.
No evidence silver hammer used to confirm the pope's death
Apr. 22nd, 2025 07:57 pmScientists Catch Star Disintegrating a Planet, Creating a Comet-Like Tail
Apr. 22nd, 2025 08:00 pmScientists have identified a planet that has a turbulent relationship with its parent star: it is being disintegrated, and leaving a spectacular trail of dusty debris in its wake. Within a few million years, the planet will be completely destroyed.
Boost Mobile Is Adding Tablets And Smartwatches
Apr. 22nd, 2025 07:43 pmYou typically get phones through carriers, but with the rise of other kinds of devices with cellular support, lines are needed for those devices as well. Most carriers offer tablet and smartwatch lines, and now, Boost Mobile is joining the fray.
What we know about claims US border protection detained, deported 2 German tourists in Hawaii
Apr. 22nd, 2025 07:40 pmCan't Wait for the iPhone 17? Here's Which iPhone You Should Get Right Now
Apr. 22nd, 2025 07:30 pmEvery year, fans and Apple enthusiasts eagerly await the new iPhones. This year, it will be the iPhone 17 that breaks cover, likely in September. But what if you need a new iPhone right now, in the middle of the company's product cycle? Let's find out which iPhone model suits you best.